Security at Bask
Enterprise-grade data protection
Trust Bask to keep your data secure and meet your HIPAA compliance requirements.
So many reasons to try, and here are some:

Identity & Device Management

Data Ownership & Protection

Information Governance

End-to-End (E2E) Encryption

Best in class
Industry-accepted best practices and frameworks
Our security approach focuses on security governance, risk management and compliance. This includes encryption at rest and in transit, network security and server hardening, administrative access control, system monitoring, logging and alerting, and more. Some say we are Shopify for HIPAA compliance.
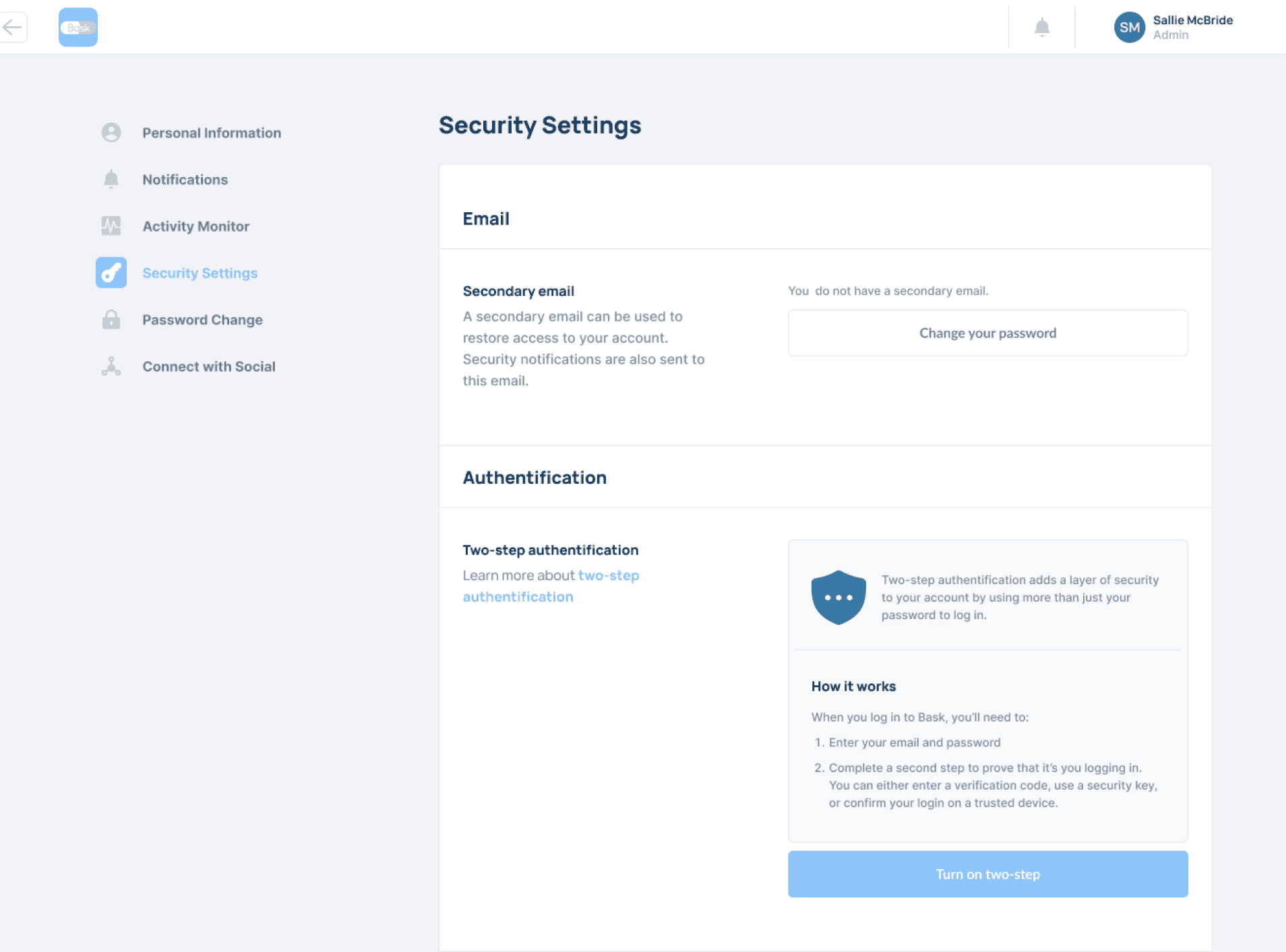

SECURITY
Work confidently with Enterprise-grade security.

Two-factor authentication controls.

Security
CONTACT: SECURITY@BASK.HEALTH

Overview
- IntroductionHow has this been accomplished?What happens if something becomes out of compliance?Procedures & ControlsSecure Policies & ProceduresVulnerability & Penetration TestingData EncryptionMulti-factor AuthenticationSecure Development LifecycleMonitoringEmployee Training & AwarenessAccess Controls & Background ChecksThird-party Audits and AssessmentsIntrusion DetectionVulnerability DisclosureOut of scope vulnerabilitiesWhat to do and what not to doHow to report a vulnerability
Date of Last Revision: 4/27/2023
As a telehealth software company that has maintained compliance with ISO 27001, SOC 2, CCPA, GDPR, and HIPAA requirements, Bask Health understands the critical importance of information security in today's digital landscape. The increasing frequency and sophistication of cyber attacks highlight the necessity for businesses to prioritize security to safeguard their data and ensure the trust and confidence of their clients. By implementing industry-standard security measures and best practices, we demonstrate our unwavering commitment to the protection of sensitive information and the preservation of the integrity of our operations. We take pride in the rigorous security protocols we have in place and are dedicated to maintaining the highest standards of security excellence.
How has this been accomplished?
As an organization, we understand the importance of maintaining compliance with security practices and standards. That's why we utilize security and compliance automation platforms to ensure that we remain continuously compliant and adhere to the relevant security protocols.
We have a centralized platform that automates the assessment and monitoring of various security controls and procedures. By integrating with our existing systems and tools, our platforms provide us with a comprehensive view of our security posture, identifying any potential issues and ensuring that we are always up to date with the latest security protocols and industry standards. This gives us the confidence that we are following industry best practices and that we are providing a secure environment for our customers and stakeholders.
What happens if something becomes out of compliance?
If something were to fall out of compliance, our compliance automation platform would detect the issue and alert us immediately. This would allow us to take prompt action to address the problem and get back into compliance quickly. By using a compliance automation platform like this, we can stay on top of our compliance obligations and take proactive steps to ensure that we remain compliant with the relevant security practices and standards. This gives us the confidence that we are providing a secure environment for our clients and stakeholders and helps us to maintain our reputation as a reliable and trustworthy organization.
Procedures & Controls
Secure Policies & Procedures
Written information security policies and procedures ensure that Bask Health has documented and tested controls in place to protect customer data and respond to security incidents effectively.
Vulnerability & Penetration Testing
Regular vulnerability and penetration testing help to identify and address potential security weaknesses before they can be exploited by attackers. Bask Health undergoes an external penetration test of our web application annually by a third party to identify any security vulnerabilities we may have, allowing us to raise these issues internally and remediate them immediately. An official report is created for Bask Health stating that the issues found are now fixed. We also conduct regular internal penetration tests. Additionally, we employ automated vulnerability scanning within our code and its dependencies.
Data Encryption
Encryption of sensitive data helps to ensure that the data cannot be accessed or read by unauthorized parties. Having our database encrypted allows customers to feel safe when using our product as it safeguards data when in transit or at rest.
Multi-factor Authentication
Multi-factor authentication helps to prevent unauthorized access to Bask Health's systems, which can help to protect customer data from theft or tampering.
Secure Development Lifecycle
Multi-factor authentication helps to prevent unauthorized access to the company's systems, which can help to protect customer data from theft or tampering. All changes to our codebase are protected with branch protection, meaning that to be able to push a new code change to production, the code change must have been approved by another engineer, as well as the code change has to pass a number of automated tests that check for security issues introduced by the code or its dependencies, as well as end-to-end testing and more. This way, no bad actors internal or external to Bask Health are able to push malicious code due to our secure reviews process.
Monitoring
Ongoing monitoring of system access logs and network traffic helps Bask Health to detect and respond to potential security incidents, reducing the likelihood of customer data being compromised.
Employee Training & Awareness
Regular training and awareness programs for employees help to ensure that they are equipped to handle customer data securely, reducing the likelihood of human error or intentional data breaches. We make it a priority that these are completed straight away for all new employees and completed annually for all existing employees.
Access Controls & Background Checks
Access controls and background checks for employees, third-party vendors, and service providers help to ensure that they are trustworthy and can be relied upon to handle customer data securely. Background checks are performed on all new hires, and the company may conduct them as a way for Bask Health to establish confidence in the employee we are choosing to hire. Additionally, only giving access to applications for particular applications is important in staying compliant. Every quarter, we review application access and access levels for all employees to make sure they only have access to applications required to perform their job role.
Third-party Audits and Assessments
Regular third-party audits and assessments provide an independent validation of the effectiveness of Bask Health's information security controls and procedures, providing customers with confidence that their data is being handled securely.
Intrusion Detection
Bask Health utilizes intrusion detection systems to continuously monitor our systems for potential threats that may occur at any time. Knowing at the early stages that a threat could be critical allows us to act quickly and efficiently to prevent any threats from causing short or long-term issues.
Vulnerability Disclosure
At Bask Health, we consider the security of our systems a top priority. But no matter how much effort we put into system security, there can still be vulnerabilities present.
If you discover a vulnerability, we would like to know about it so we can take steps to address it as quickly as possible. We would like to ask you to help us better protect our clients and our systems.
Out of scope vulnerabilities:
- Clickjacking on pages with no sensitive actions.
- Unauthenticated/logout/login CSRF.
- Attacks requiring MITM or physical access to a user's device.
- Any activity that could lead to the disruption of our service (DoS).
- Content spoofing and text injection issues without showing an attack vector/without being able to modify HTML/CSS.
- Email spoofing
- Missing DNSSEC, CAA, CSP headers
- Lack of Secure or HTTP only flag on non-sensitive cookies
- Deadlinks
Note: Bask Health reserves the right to designate any reported vulnerability as out of scope.
What to do and what not to do
- Do not run automated scanners on our infrastructure or dashboard. If you wish to do this, contact us and we will set up a sandbox for you.
- Do not take advantage of the vulnerability or problem you have discovered, for example by downloading more data than necessary to demonstrate the vulnerability or deleting or modifying other people's data,
- Do not reveal the problem to others until it has been resolved,
- Do not use attacks on physical security, social engineering, distributed denial of service, spam or applications of third parties
How to report a vulnerability
You can report vulnerabilities by email to security@bask.health. Once we have received your email, there may be a delay in getting back to you while our team triages the issue.
Please provide sufficient information to reproduce the problem, so we will be able to resolve it as quickly as possible. Usually, the IP address or the URL of the affected system and a description of the vulnerability will be sufficient, but complex vulnerabilities may require further explanation.
- If you have followed the instructions above, we will not take any legal action against you in regard to the report
- We will handle your report with strict confidentiality, and not pass on your personal details to third parties without your permission
- We will keep you informed of the progress towards resolving the problem
- In the public information concerning the problem reported, we will give your name as the discoverer of the problem (unless you desire otherwise)
- We strive to resolve all problems as quickly as possible, and we would like to play an active role in the ultimate publication on the problem after it is resolved.
Start today and change everything
The security program at Bask protects our organization and your data at every layer
